Valdoria Votes – KC7 Cyber Challenge
Navigate the tension-filled cybersecurity scenario of an election under threat in “Valdoria Votes.” Enhance your KQL skills as you investigate infiltration attempts aimed at undermining the voting process.
🔍 Overview
The What’s a query? section is the first part of the KC7 Cyber Challenge Module 335.
📚 Module Structure
This challenge is divided into five parts:
- What’s a query
- All about the dataz
- A vote of no confidence
- Snooping Around
- Look on my [Security], ye Mighty, and despair!
Each section builds on the last. For example, you may uncover an IP address or user account in one task that becomes the key to solving several others.
What’s a query
Let’s Get Familiar with the team at Valdoria Board of Elections.
The Employees table contains information about all the staff who are part of the Valdoria Board of Elections.
We’ll use KQL (Kusto Query Language) queries to explore our data. Don’t worry, we’ll provide you with some queries to get started with the game.
For each query we provide, you can simply copy and paste it into the query pane on the right, and then click run.
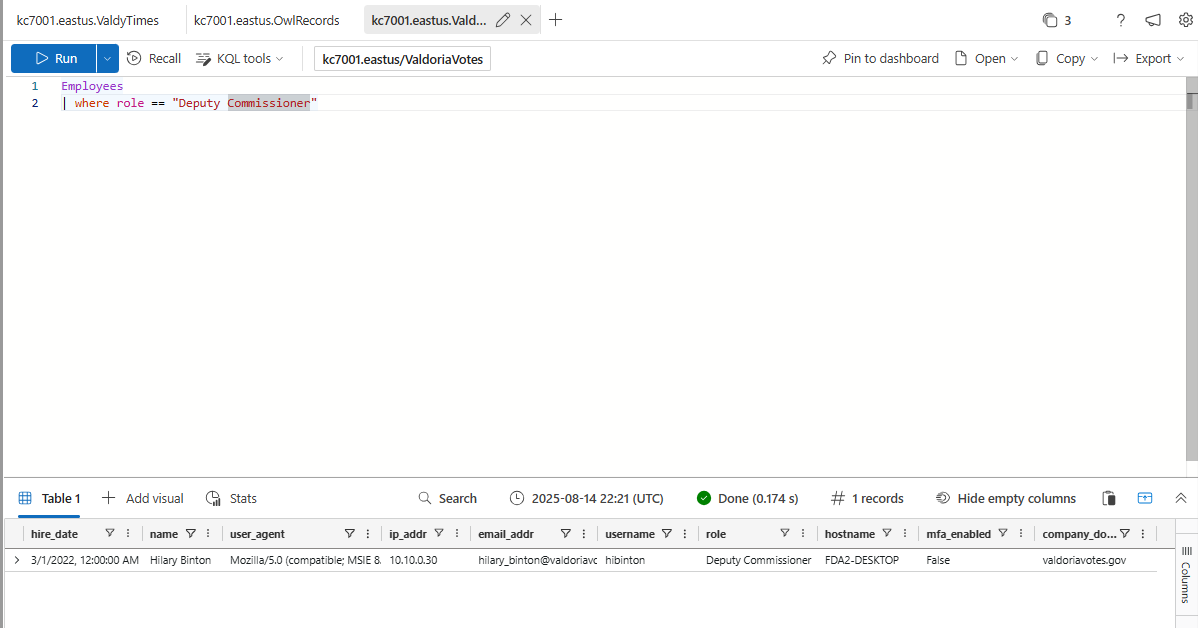
What is the name of the Deputy Commissioner?
Hilary Binton
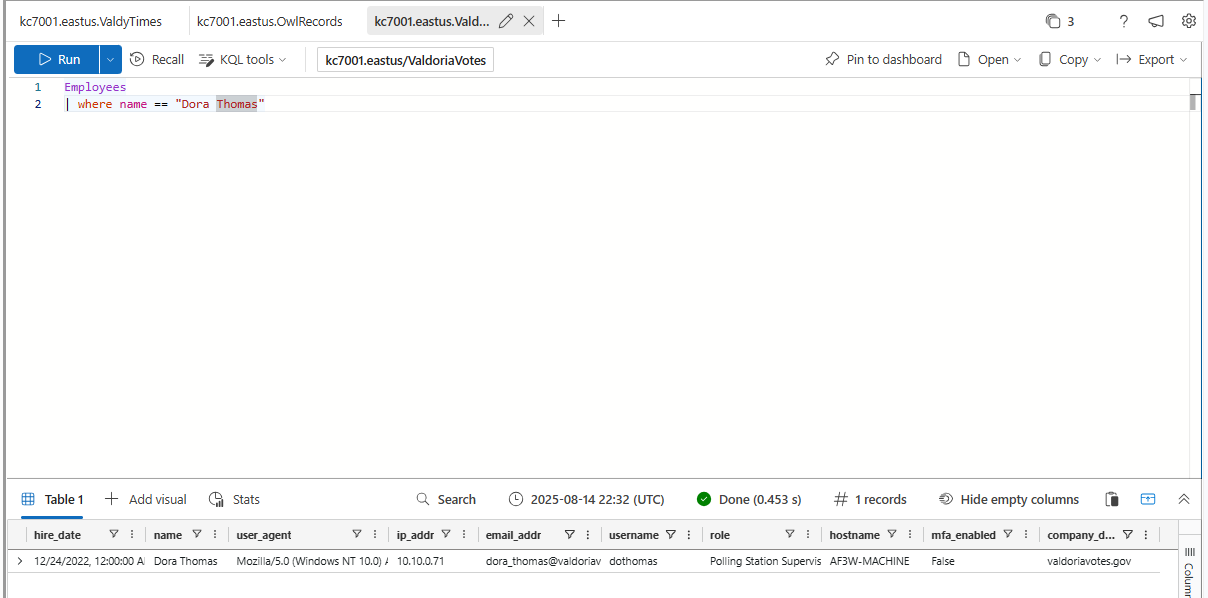
What is Dora Thomas’ role?
Polling Station Supervisor
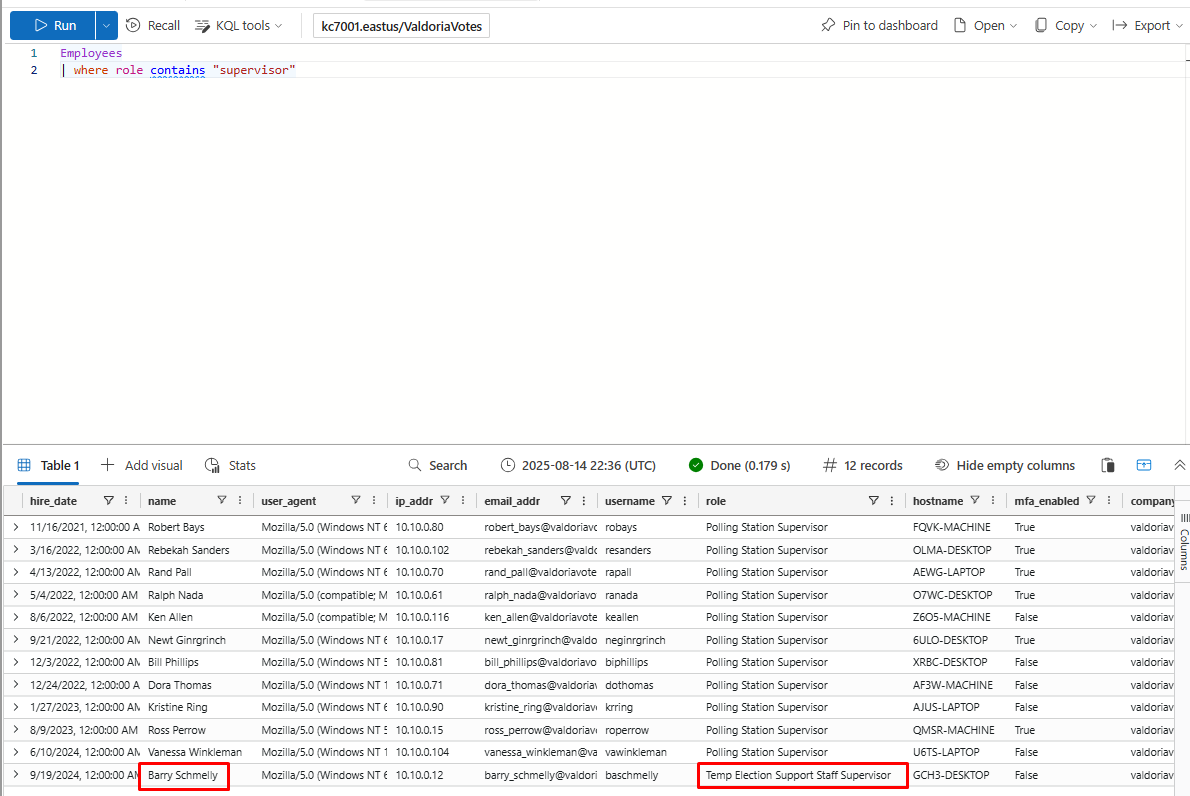
What is this supervisor’s name?
Barry Schmelly
What is Barry Schmelly’s IP address
10.10.0.12
What is Barry Schmelly’s hostname
GCH3-DESKTOP
What is Barry Schmelly’s email address?
barry_schmelly@valdoriavotes.gov
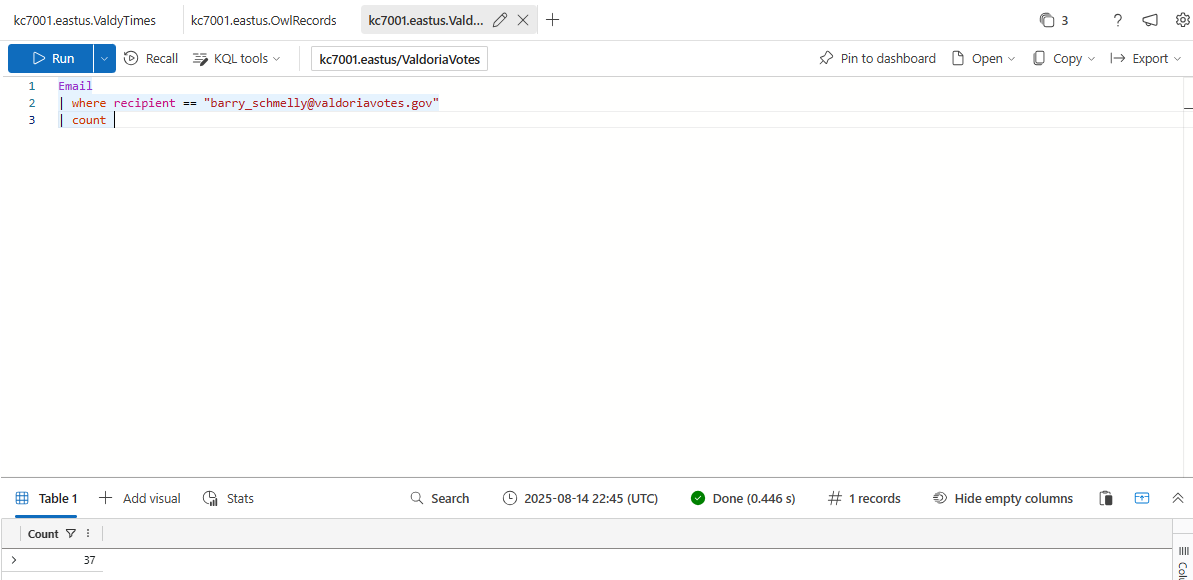
How many emails did Barry Schmelly receive?
37
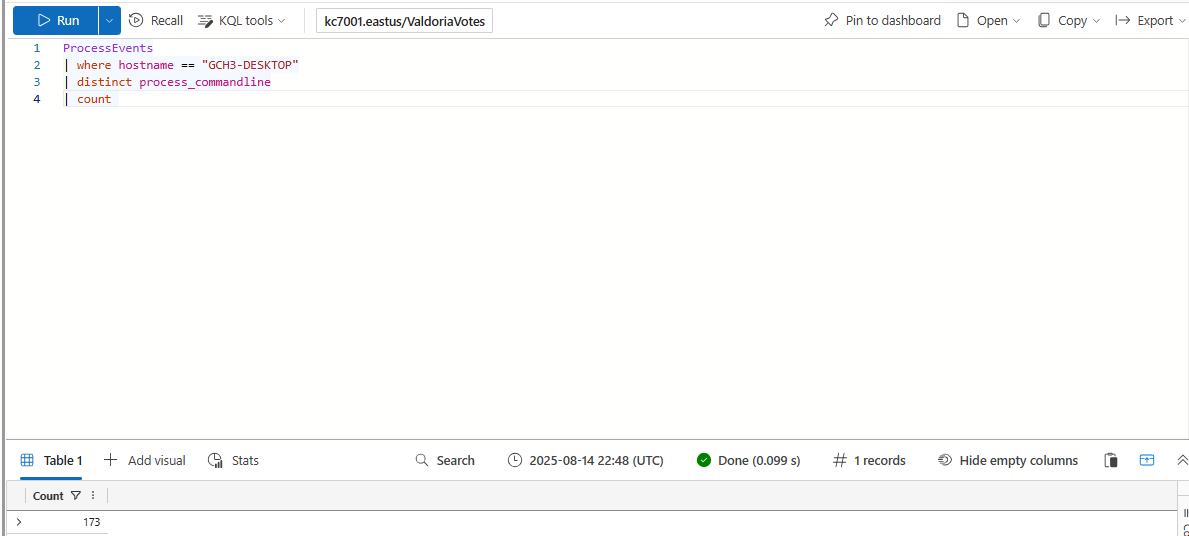
How many distinct commands were run on Barry Schmelly’s machine?
Sometimes, you’ll want to look at multiple items at once in another table. You can’t be expected to type all of those items by hand, or even to look for them one by one. That’s where let statements can save you time! A let statement allows you to save values in a variable that you can then access easily by calling the variable in your query. Let’s try an example.
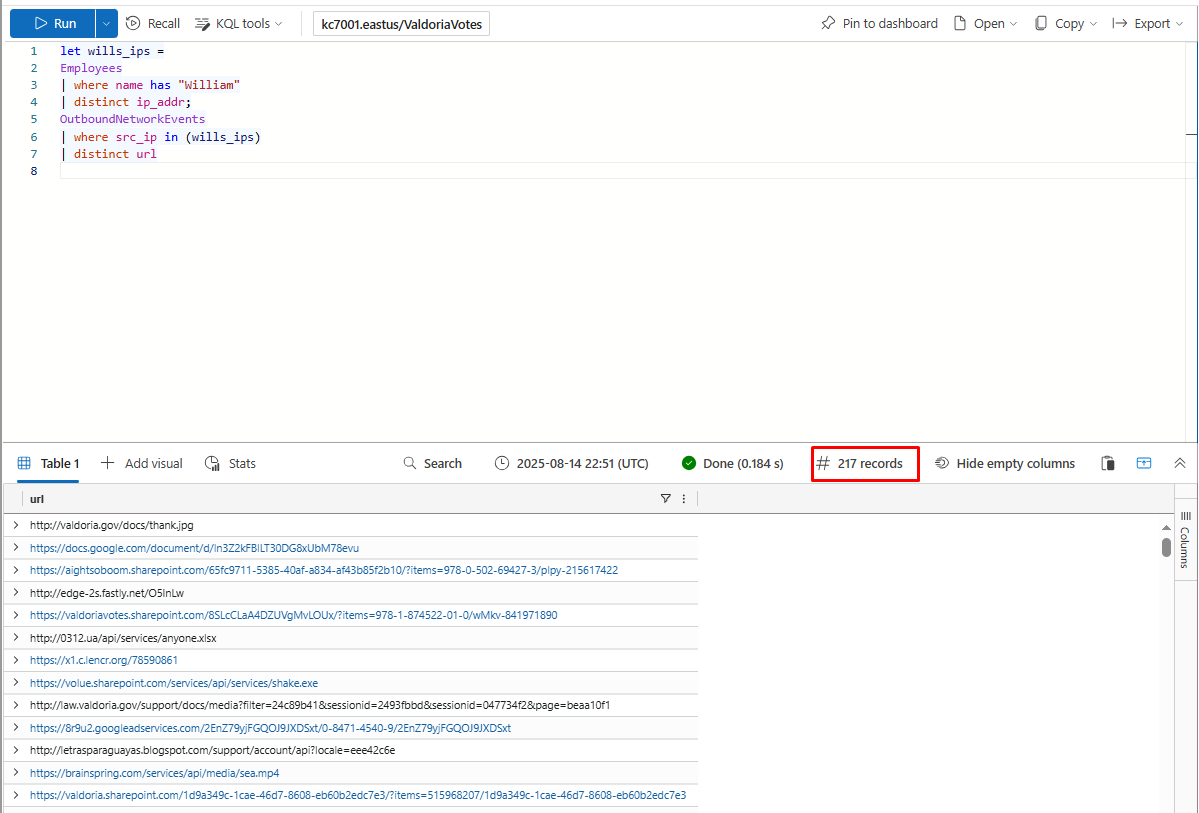
What if we wanted to see all the URLs browsed by employees with the name William? To find it we’d need to find all their IP addresses. But there are so many Williams! Instead of typing each one in separately, we can save the IP addresses in a let statement, like so:
How many distinct URLs did employees with the first name William visit?
217
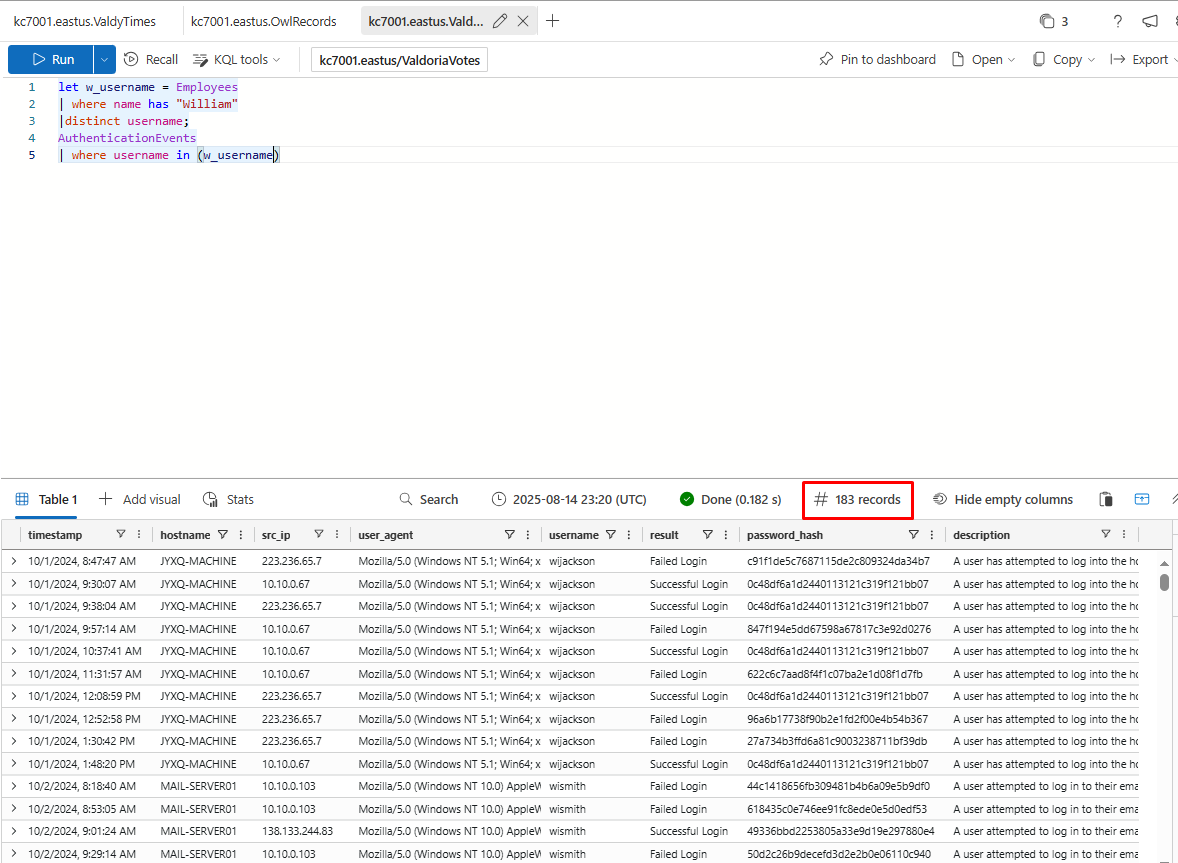
How many authentication attempts did we see to the accounts of employees with the first name William?
183
By grabbing just the first 10 rows, you can get an overview of the structure and contents without having to sift through massive amounts of data. This helps you decide where to focus your investigation and identify any key patterns or anomalies early on.
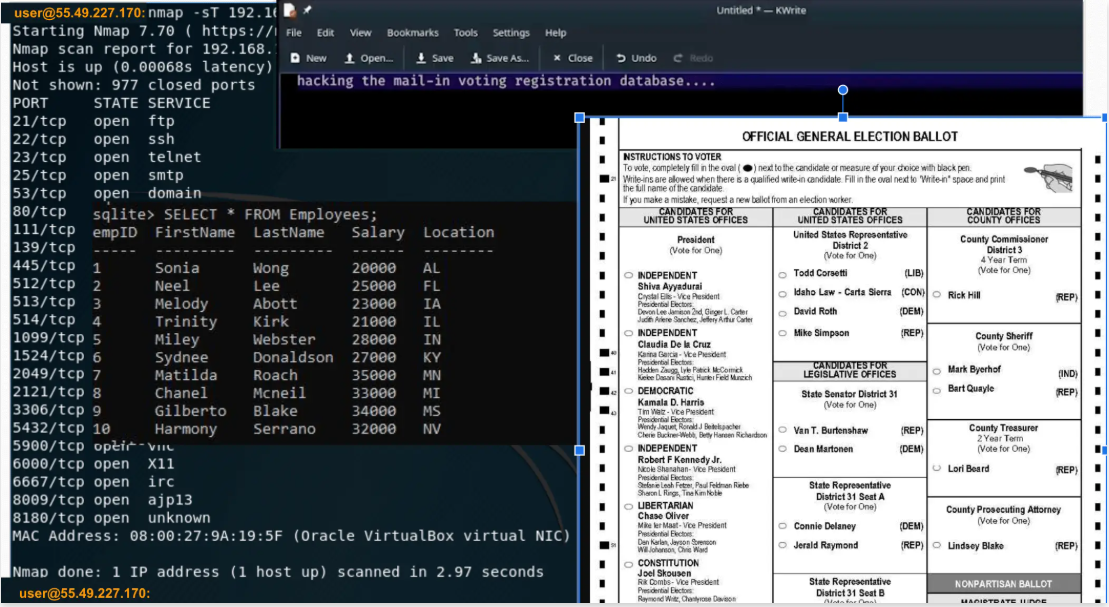
What IP address did they forget to hide in the poster?
55.49.227.170
Is there any evidence of traffic from this IP address to our network? (yes/no)
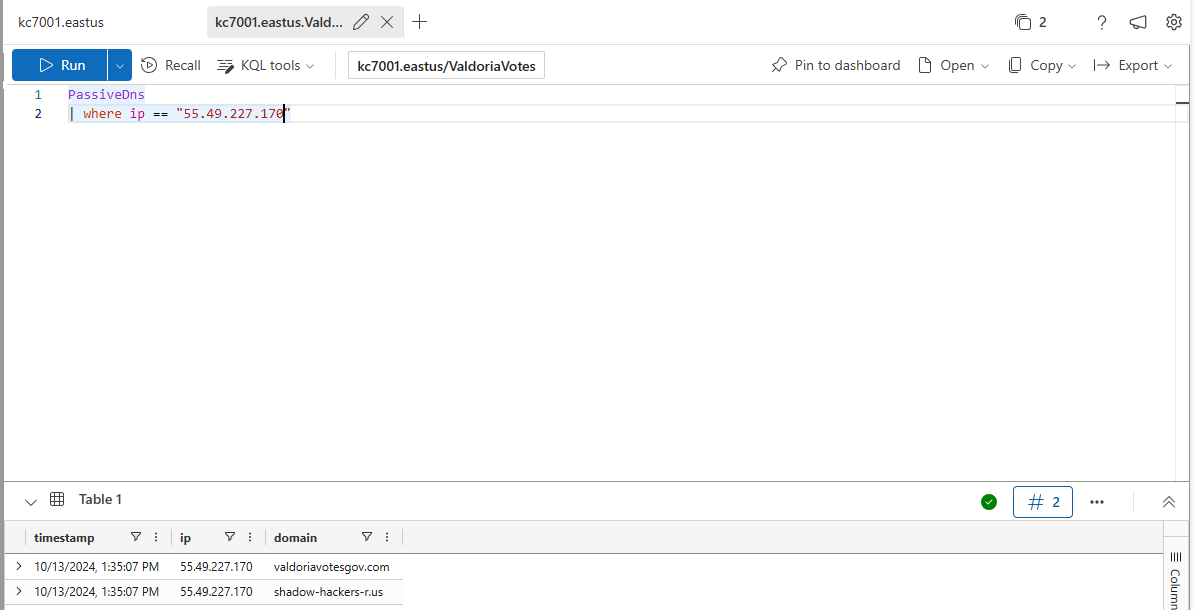
PassiveDNS is a tool that keeps a record of which domain names (like websites) have been connected to specific IP addresses over time. This allows us to look back and see which websites or services might have used a particular IP, helping us track any suspicious or malicious activity
How many domains resolved to the IP 55.49..*?
2
What is the Valdoria related domain resolving to that IP?
valdoriavotesgov.com
What is the legitimate domain for the Valdoria Elections Board?
valdoriavotes.gov
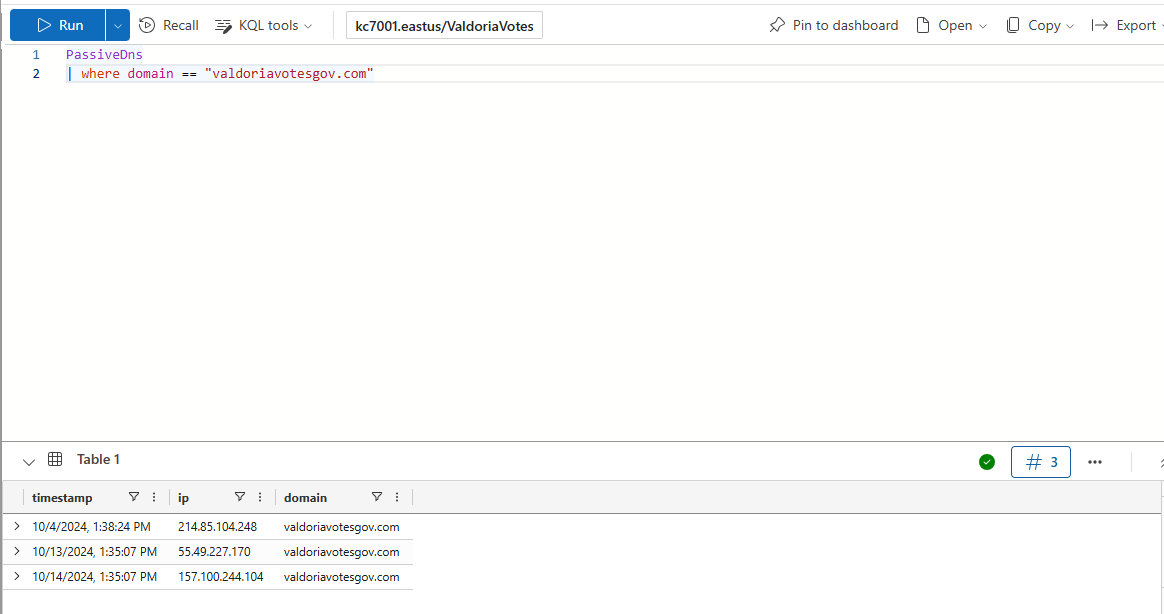
Let’s pivot on the fake Valdoria domain to see if it’s been associated with other IPs.
How many IP addresses did the fraudulent Valdoria government domain resolve to?
Which table should we be looking at for records of that kind of activity again?
InboundNetworkEvents
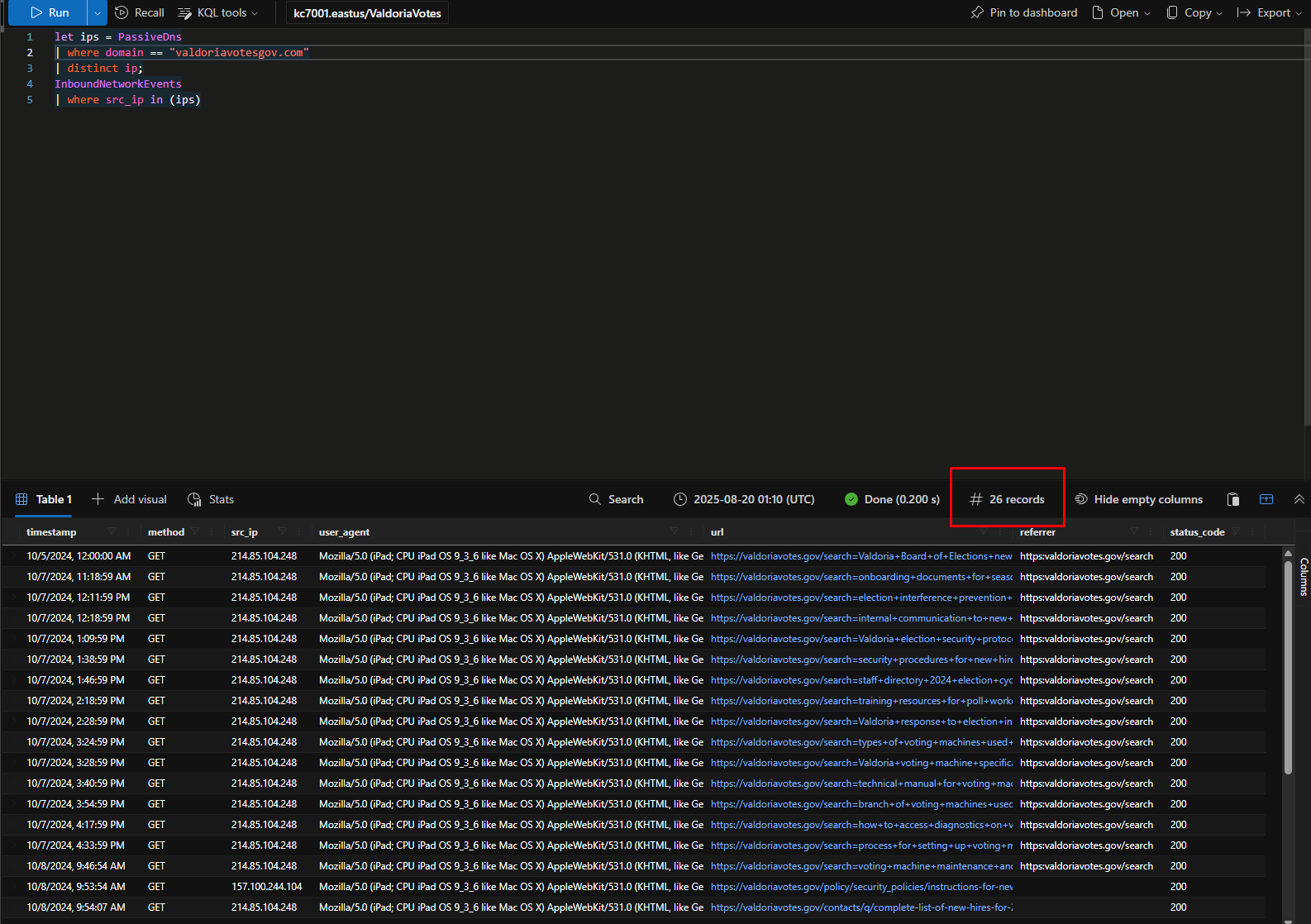
How many requests do we see to our network from those IPs?
Which phase of the Cyber Kill Chain is this called?
recon;reconnaissance
We can learn a lot more about the threat actor’s motives by analyzing their browsing history. Let’s dig deeper!
In the first record we have of their activity, the hackers seemed focused on learning more about a certain group at the Valdoria Board of Elections.
What group were they specifically interested in?
new hires
They left a pretty clear clue about their intentions by researching our ability to prevent malicious activity.
What specific area of our prevention measures were the threat actors interested in?
election interference
We’re onto them and starting to get a clearer picture of their plans! Let’s keep digging through their browsing history to see exactly how they intended to interfere with the election.
What important machines were the hackers trying to get into? (two words)
voting machines
The hackers even tried to locate a specific document that would reveal exactly how the machines operate.
With this information—like configuration details or default passwords—they could create a more effective plan to hack the machines.
Which document were the hackers looking for? (two words)
technical manual
So we know they were targeting voting machines, but did they actually succeed?
Let’s look for evidence in our data. Remember, there was a suspicious-looking Valdoria domain registered by the adversaries.